Necessary Actions When Updating or Upgrading to 7.16
Necessary Actions When Updating/Upgrading
This page describes the actions that you must manually execute when updating from version 6.x to a newer version. It also lists things that you must pay special attention to. An update to a new version that skips some of the previous versions is possible and does not require updating to each version in between. However, in this case, you must carry out all the actions from your previous version to the target version in the order listed here.
6.16 --> 7.0
- Manual steps are mandatory. See How to upgrade to yuuvis RAD 7.0 for a step-by-step guide.
7.10 --> 7.12
- The new repository manager 4 (replacement for the ERM but ERM is still available) is added to the service-manager as a microservice. Further information can be found at https://help.optimal-systems.com/yuuvisRAD/v70/sap/de/index.htm
To complete the installation: - Edit the file <service-manager>\config\servicewatcher-sw.yml
Add the following section:
- name: repositorymanager
type: microservice
profiles: prod,cloud,mq
instances: 0
arch: x64
memory: 768M
port: 8010
path: "${appBase}/repositorymanager/repositorymanager-app.jar"- To use the new microservice, set the instances property to 1, else leave it at 0.
- The new repository manager 4 (replacement for the ERM but ERM is still available) is added to the service-manager as a microservice. Further information can be found at https://help.optimal-systems.com/yuuvisRAD/v70/sap/de/index.htm
7.12 --> 7.14
- It is now possible to encrypt all passwords stored in the configuration files of the service-manager. For fresh installations the setup will do the encryption by default, for existing installations follow the below steps to encrypt the passwords.
The encryption is optional and doesn't have to be done.- Open a command prompt (cmd.exe) and navigate to the folder <service-manager>\tools
- Copy the plaintext password you want to encrypt
- Execute "encode.bat <plaintext_password>" (without < >)
Replace the plaintext password in the configuration file with the return value of the form ENC(<characters>) (do not omit ENC( ))
The encrypted passwords can not manually be decrypted anymore. Note the plaintext passwords at a safe location before overwriting them.
Repeat these steps for all passwords you want to encrypt. The following configuration files support encryption: archive-prod.yml, application-dbs.yml, application-es.yml, application-red.yml, erm-prod.yml, gateway-prod.yml, repositorymanager-prod.yml, servicewatcher-sw.yml
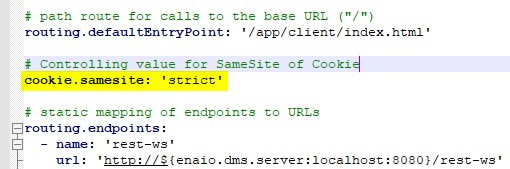
- The gateway can now optionally set the samesite cookie policy level as described here: https://blog.chromium.org/2019/10/developers-get-ready-for-new.html. To define it do the following:
- Edit the file <service-manager>\config\gateway-prod.yml
- Add a new line with "cookie.samesite: '<level>' " → replace <level> with your desired policy level. It can be one of 'none', 'lax' or 'strict'.
- It should now look like this:
- It is now possible to encrypt all passwords stored in the configuration files of the service-manager. For fresh installations the setup will do the encryption by default, for existing installations follow the below steps to encrypt the passwords.
7.14 --> 7.16
- The gateways behaviour when calling the /logout endpoint has changed from always answering with http code 304 and redirecting to /login?logout to now return http code 200 or 304 and redirection to a passed url if and only if this was passed with the 'redir' query parameter.
- Behaviour before:
- call to /logout (without parameter): HTTP 304 with redirection to /login?logout
- call to /logout?redir=url: HTTP 304 with redirection to url (url can be any value)
- Behaviour now:
- call to /logout (without parameter): HTTP 200 (no redirection)
- call to /logout?redir=url: HTTP 304 with redirection to url (url can be any value)
- This is especially important if you have an external tool that creates sessions by sending the basic auth header and you want to close this session by calling /logout. With the before behaviour the http client would get redirected to the login page and automatically create a new session because the basic auth header is existent. This could be avoided by setting the redir parameter to (e.g.) '/auth/info/'. This is not necessary anymore.
Custom clients
Custom clients need to make sure that when calling logout you set the redir parameter to redirect to the login-form again. Otherwise the session gets logged out but the client still shows the current page (or an error).
- Behaviour before:
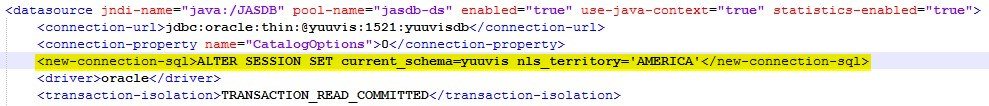
- Oracle databases only: The NLS_TERRITORY session setting must be configured to 'AMERICA' in order for date/time values to be processed correctly. To make sure this is the case, do the following:
- Edit the file <core-service>\standalone\configuration\standalone-full-ha.xml.
- Find the subsystem 'datasources:5.0' and there the datasource with jndi-name="java:/JASDB".
- Within this section find (or if necessary create) the following line:
<new-connection-sql>ALTER SESSION SET current_schema=yuuvis</new-connection-sql> (yuuvis is a placeholder for the actual schema name) - Add the parameter nls_territory='AMERICA' after "current_schema=yuuvis".
- The section should now look as shown below:
Metrics-Manager only: Due to CVE-2021-44228 (a.k.a Log4Shell) and CVE-2021-44832 the metrics-manager needs to be updated to the newest hotfix. Please see https://help.optimal-systems.com/rw/en/index.html for details.
- The format of the response body of the
BpmProcessService.getDataFieldsendpoint changed from the examplary value "l_workflowFileIds.item: OsId[id=97DC54B56A844F9EBB198935476F15B5]" to "l_workflowFileIds.item: 97DC54B56A844F9EBB198935476F15B5".
Custom microservices that use this endpoint need to adapt to this change before updating to version 7.16.
- The gateways behaviour when calling the /logout endpoint has changed from always answering with http code 304 and redirecting to /login?logout to now return http code 200 or 304 and redirection to a passed url if and only if this was passed with the 'redir' query parameter.